Illinois-developed tool to help analyze, secure nation’s power systems
Two University of Illinois professors are commercializing a tool that analyzes security vulnerabilities in networked systems. The tool, which will be marketed under the name NP-View, will help secure the nation’s power companies, which are increasingly under attack from hackers.
Illinois professors and TCIPG researchers David M. Nicol and William H. Sanders have co-led the development of the network access policy tool, a version of which was developed at Illinois under the name NetAPT. The creators recently received a U.S. patent for the design of the tool, while the U.S. Department of Homeland Security has provided funding for a one-year effort to commercialize it.
Misconfiguration of firewalls and other local security mechanisms is a major source of security vulnerabilities in computing systems. The complex interactions involved in distributed and layered policy implementations can lead to subtle errors and mask problems. NP-View was designed to perform an automated, comprehensive security policy analysis to identify any respects in which an implementation deviates from global access policy. It has an intuitive user interface and requires minimal setup time, so system administrators with ordinary skill sets can easily use the tool.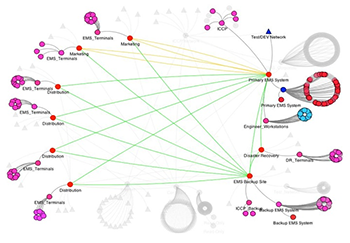
"Modern computer systems can be staggeringly complex-- far too large and complicated for anyone to analyze by hand," explains Nicol, who directs the Information Trust Institute (ITI) at Illinois. "And yet we have to be able to verify their security posture, because so-called 'critical' systems literally are critical. If they fail, there can be terrible financial and human consequences. We developed NP-View to fill the need for a tool that can automatically obtain an overview of a network's policy implementation, and compare it to the policy that's supposed to be in place. Any divergences between the two are potential problems that administrators need to look at."
Some of the tool’s development took place in ITI's Trustworthy Cyber Infrastructure for the Power Grid (TCIPG) project, of which Sanders is the director. Its mission is to improve the way power grid cyber infrastructure is built. As part of the TCIPG effort, the beta version was installed and used by power industry partners in their actual control systems in order to evaluate their systems' compliance with access control policy. The software in fact found previously undetected implementation flaws-- flaws that were compromising the security of major industrial systems that were already in operation.
One company that has used the tool is Lafayette (La.) Utilities, which implemented the NetAPT version within the past year and has used it to evaluate their network's potential vulnerabilities and view the paths of cyber traffic in and out of the system.
"Before we make any actual changes to our firewall, it's helpful to be able to model it in NetAPT and see how it will affect our network," said Dan Barry, network engineer for the utility. "It's also a great way for less technical people to get a good idea of our network security. If I show someone a text file of a configuration, it will to take forever to go through it. But NetAPT generates a map of the network and you can trace the traffic, making it simple to explain."
“Our success in industry settings is a clear demonstration of the technology’s value,” says Nicol. “It’s a powerful tool for identifying communication paths that have been left open in a system, despite not being needed by the system's legitimate traffic, as outlined in the access policy. Such needlessly open paths are invitations for malicious exploits.”
In recognition of the potential importance of the tool in ensuring security of critical cyber infrastructures, the U.S. Department of Homeland Security announced funding for a one-year effort to support commercialization of NP-View. The team is using the funds to develop additional training materials, enhance user support, and increase the value of the software by adding new functionalities that will be useful to some types of user. The researchers are launching a start-up called Network Perception to offer NP-View to the broader marketplace. It will remain available for academic use under its beta name, NetAPT.
"There's a huge potential audience for this tool," Nicol says. "Anyone who's responsible for protecting critical cyber infrastructure using firewalls would want the analysis we can provide. We're excited by the opportunity DHS is giving us to get our technology in those people's hands."
The U.S. patent, entitled "Analysis of Distributed Policy Rule-sets for Compliance with Global Policy" (Patent No. US 8,209,738 B2) has been awarded to Nicol, Sanders, research programmer Mouna Bamba, and Sankalp Singh, a recently graduated University of Illinois student whose Ph.D. effort was largely directed towards development of this technology. Nicol and Sanders are both professors on the faculty of the Department of Electrical & Computer Engineering at Illinois. ITI, which Nicol directs, is focused on designing trustworthy systems to secure the nation’s critical infrastructures. Sanders, former director of ITI, was recently named interim head of the Department of Electrical and Computer Engineering, previously serving as director of the Coordinated Science Laboratory.
The Homeland Security funding award is entitled "A Tool for Compliance and Depth of Defense Metrics," award FA8750-12-2-0233.
